本文最后更新于 489 天前,其中的信息可能已经有所发展或是发生改变。
[Week 2] 报告哈基米
- 得到一张png图片,先用StegSlove查看LBS隐写,在最低限位上看到了参数信息
- a,b=7,35 (a,b=35,7),shuffle_times=1
- 然后用010editor打开发现在结尾有一段hint
- Maybe You Need To Know Arnold Cat
- 得到是经过Arnold变换的图像
- 采用了大佬的脚本,进行了修改
from PIL import Image
import numpy as np
def arnold_decode(image, shuffle_times, a, b):
""" Decode for RGB image that encoded by Arnold
Args:
image: rgb image encoded by Arnold (numpy array)
shuffle_times: how many times to shuffle
a: parameter a for Arnold's cat map
b: parameter b for Arnold's cat map
Returns:
decode image (numpy array)
"""
# 1: 创建新图像
decode_image = np.zeros_like(image)
# 2: 计算N
h, w = image.shape[0], image.shape[1]
N = h # 或N=w
# 3: 遍历像素坐标变换
for time in range(shuffle_times):
for ori_x in range(h):
for ori_y in range(w):
# 按照公式坐标变换
new_x = int(((a * b + 1) * ori_x + (-b) * ori_y) % N)
new_y = int(((-a) * ori_x + ori_y) % N)
decode_image[new_x, new_y] = image[ori_x, ori_y]
return decode_image
path = "./mijiha.png"
image = np.array(Image.open(path))
decoded_image = arnold_decode(image,1,35,7)
decoded_image_pil = Image.fromarray(np.uint8(decoded_image))
output_path = "decoded_image.png"
decoded_image_pil.save(output_path)
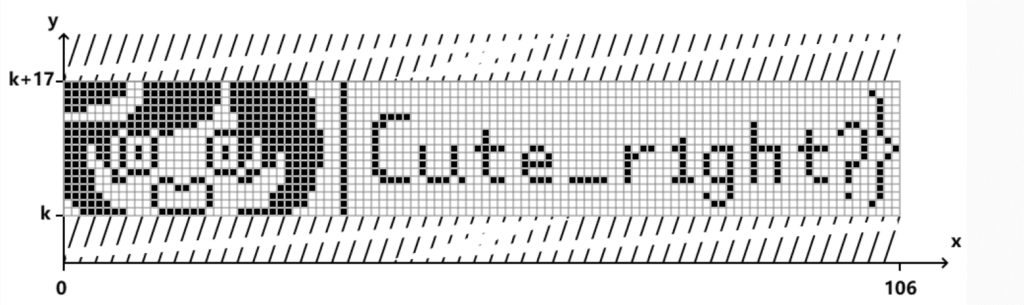
- 得到的图像上只有半个flag
- 0xGame{hajimi_i5_
- 此外注意到010editor打开中结尾有txt字样
- 仔细观察发现是倒序的PK开头字样,判断是zip压缩包
- 手写脚本
def reverse_file_bytes(input_file, output_file):
with open(input_file, 'rb') as f:
byte_data = f.read()
reversed_data = byte_data[::-1]
with open(output_file, 'wb') as f:
f.write(reversed_data)
print(f"Reversed bytes have been written to '{output_file}'.")
input_path = "./mijiha.png" # 替换为输入文件路径
output_path = "./mijiha.bin" # 替换为保存的输出文件路径
reverse_file_bytes(input_path, output_path)- 然后用binwalk分离
- 打开压缩包查看txt
- 第一行为hint提示Tupper公式(塔珀自指公式)
- 同时能发现字是逆序的,猜测数字也是逆序的
- 使用-网站-转换tupper公式
- 得到后半段Cute_r1ght?}
[Week 2] 我叫曼波
- 观察python文件发现经过RC4加密,然后转化为3进制,在用对应的字典替换
- 同时RC4是对称加密,调用即可解密
- 先写脚本,获得加密后的密文以及对应密钥
from pwn import *
p = remote('47.98.178.117', 1111)
while True:
try:
p.recvuntil(b'>')
p.sendline(b"1")
test = p.recvline().decode().split("\n")
if test == "You've reached the end of flag.Good Luck!----MANBO":
break
p.recvuntil(b'>')
p.sendline(b"2")
key = p.recvline().decode().split("\n")[0][1:]
p.recvuntil(b'>')
p.sendline(b"3")
c = p.recvline().decode().split("\n")[0][1:]
keys += [key]
cs +=[c]
except Exception as e:
break
print(cs)
print(keys)- 编写解密脚本
from Crypto.Cipher import ARC4
manbo_dict = {"曼波":"0","哦耶":"1","哇嗷":"2"}
keys = [?]
cs = [?]
def RC4(plain,K):
S = [0] * 256
T = [0] * 256
for i in range(0,256):
S[i] = i
T[i] = K[i % len(K)]
j = 0
for i in range(0,256):
j = (j + S[i] + ord(T[i])) % 256
S[i], S[j] = S[j], S[i]
i = 0
j = 0
cipher = []
for s in plain:
i = (i + 1) % 256
j = (j + S[i]) % 256
S[i], S[j] = S[j], S[i]
t = (S[i] + S[j]) % 256
k = S[t]
cipher.append(chr(ord(s) ^ k))
return ("".join(cipher).encode()).decode()
def decode(c,key):
base3 = ''
base6 = ''
for i in range(0,len(c),2):
base3 += manbo_dict[c[i:i+2]]
for i in range(0,len(base3),5):
base6 += chr(int(base3[i:i+5],3))
base6 = base64.b64decode(base6).decode()
res = RC4(base6,key)
return res
for i in range(len(cs)):
ans += decode(cs[i],keys[i])
print(ans)- 0xGame{OH_yEah_Wow_Duang_HajiMi_u_MADE_it!_and_MaY_5e_Y0u_hAv4_HeArD_7he_ST0ry_0f_Gu_Gao_MaN_B0}
[Week 2] 呜呜呜~我再也不敢乱点了
- 打开流量包,首选项导入已给的TLS密钥
- 追踪http流,截获压缩包zip
- 解压发现有一个powershell脚本和一个bat批处理文件
- 批处理文件中暗地运行了powershell脚本
- 查看脚本(出题人真好心,帮我们都把命令注释掉了
- 明面上没有问题,用010打开查看HEX发现后续隐藏了字符
- 截取1174[496h]~2237[8BDh]之间的字符
- 这是base64加密,解密得到一个反向 shell 脚本
- 其中就能看到监听服务器的ip192.168.93.132
- MD5加密得到flag
- 0xGame{63e1de9c00fd0dccda8a2d76475ac44a}